Why I Built a Privacy-First Workout Tracker (Gym Bag Digital)

Gym Bag Digital is an offline workout tracker for Android, by me. But why? There are a couple reasons I created the Gym Bag Digital Android app.
How to Become an IBM HBCU Ambassador

In 2022, the Biden-Harris administration's White House Initiative for Historically Black Colleges and Universities (HBCUs) resulted in the creation of IBM Cybersecurity Leadership Centers in over a dozen HBCUs. The student leaders in these HBCUs are known as IBM HBCU ambassadors. These HBCU students are liaisons between their respective universities and IBM professionals focused on education equality. This relationship grants unique opportunities for networking, mentorship, resources, and future opportunities. Want to be an IBM HBCU ambassador? Here's how you can lead your HBCU.
What Should an HBCU Cybersecurity Club Do?

Cybersecurity affects every industry, including emerging technologies like artificial intelligence (AI) and quantum computing. Therefore, all Historically Black Colleges and Universities (HBCUs) should have a cybersecurity club. An HBCU cybersecurity club doesn't need to be led by a cybersecurity or STEM student. The leaders need to be passionate about IT security, data privacy, and community development. I believe such student organizations should do some things to start.
Best IBM SkillsBuild Courses for IBM HBCU Ambassadors

Part of Biden-Harris's Historically Black College and University (HBCU) cybersecurity initiative, the IBM HBCU Ambassador program began in January 2023. IBM HBCU ambassadors are charged with spreading the word of IBM's resources, including meeting and IBM SkillsBuild badge courses, among HBCU students and of course, setting the example. As a former IBM Norfolk State University (NSU) ambassador, I'll share 10 online, self-paced IBM SkillsBuild courses I recommend IBM HBCU ambassadors prioritize when building their Credly badges portfolio for professional development.
What You Should Do on Cyber Monday 2024

Throughout your quest to shop Cyber Monday deals, I want you to complete some productive tasks unrelated to consumerism. This is not about the best Cyber Monday deals in your favorite stores. This is a short, easy to-do list for increasing your data security and privacy. No, you can't prevent cyber attacks and identity theft. You can mitigate it and be proactive about knowing when you've been affected.
5 Cybersecurity Issues to Watch in 2024

Between the IBM
Saw X Was Great, Until the End

I've been a fan of Liongate's Saw franchise for years, not because of the gore, but because of the stories behind the traps which influence victims' decisions. I know, many people have a hard time getting past the red room-esque murder scenes. Each Saw movie, including Chris Rock's "Spiral," has at least one sociopolitical theme that was prominent around the time of its release, though. Saw X, whether intentional or not, had some tropes that bother me. Spoilers ahead.
Safe, Secure, and Trustworthy Artificial Intelligence But Not For You

In 2023, the Biden-Harris administration quietly released an Artificial Intelligence (AI) Bill of Rights and executive order on securing AI, Executive Order 14110 (Safe, Secure, and Trustworthy Development and Use of Artificial Intelligence). Both are quite long reads. Although I share my thoughts on them below, I recommend reading both if you're interested in the topic.
Pacemakers, Medical Devices, and Cyberbiosecurity

Pacemakers are one of the most commonly used medical embedded systems in homes today. With the strides in wireless networking, pacemakers have evolved into mobile electrocardiogram (ECG/EKG) machines, tracking patients' cardio activity remotely to assist doctors with heart health treatments [1]. These now networked embedded systems are unfortunately developed without serious effort given to cybersecurity. There have been many incidents within the past decade highlighting such vulnerabilities and their potentially fatal effects.
Norfolk State University (NSU) IBM Partnership

In September 2022, Norfolk State University (NSU) released a news post announcing the IBM NSU cybersecurity partnership. This is part of Biden-Harris' White House initiative to allot more resources and professional development opportunities to students within Historically Black Colleges and Universities (HBCUs), specifically related to information technology (IT). Four months later, I was entrusted with the role as IBM NSU student ambassador. I've since completed many free IBM courses and released content in an effort to bring more HBCU students' attention to these resources. Course topics include cybersecurity, artificial intelligence (AI), cloud computing, IBM products, and more.
What is an IBM HBCU Ambassador?
Starting with the basics, what is an HBCU? "HBCU" stands for "Historically Black College and University" (in the USA). How many HBCUs are there? At least 100, mostly in the south-eastern US. You likely know of the IBM technology corporation. But what is an IBM HBCU ambassador, also and why is it important for native Black Americans?
From the PPW and ERB to Veteran Badges?

Army veterans understand the importance of making sure your authorized awards match your Army promotion points, promotion point worksheet (PPW) and other paperwork. Those awards and badges provide a snapshot of your experiences. Once you leave the service, that concept is still applicable to some business ventures and career goals.
How to Manage Email

Electronic mail isn't going away anytime soon, no matter how many social media platforms and other businesses integrate private messaging systems. Below are a few tips to lessen the dread you might feel when looking at your inbox. No matter how long you wait to check, "you've got mail."
10 Cybersecurity Specialists to Follow

Most of what I learn about cybersecurity comes from personal research to solve issues and the ten cybersecurity specialists listed below on Twitter.
How Military Veterans Can Protect Themselves From Phishing and Other Online Scams

Military veterans are prime targets for personally identifiable information (PII). Businesses seek our Post 9/11 GI Bill because it's sure money. Employers see us as tax breaks. For as many benefits as we get between Veterans Affairs (VA) and the GI Bill, plenty others get an interesting bit of benefits from our presence. This is one of many reasons as to why military service members must be careful of how we share our military info.
Don't worry, non-technical folks, as I've done my best to simplify the best security practices, these days sometimes called the "Zero Trust" mindset, that I'll recommend in the key takeaways and video below. The overall solution: verify contacts supposedly from VA medical centers and community-based outpatient clinics (CBOCs).
Security-Focused Operating Systems

The world has reached a point where the frequency of cyber attacks is gradually influencing people to choose security over convenience and bleeding edge technology. Many are switching from Android smartphones to iPhones or basic flip phones, sometimes referred to as "feature phones." Some are replacing Windows personal computers (PCs) with Apple MacBooks. Individuals more serious about cybersecurity are migrating to Unix-based operating systems (OSes). The reason why is simple. Windows is attacked at a significantly higher rate than macOS, Linux, and other Unix-based OSes combined because it is most prominent in homes and corporate offices. According to DistroWatch.com, there are over three hundred BSD and Linux OSes, but few are built specifically with the goal of increased high security and privacy [1]. Two of the most interesting security-focused OSes in active development today: OpenBSD and Qubes OS.
How to Protect Company Data and Why It Might Not Be Enough

Protecting the company's data and physical assets is everyone's job, much like customer service. Laws and regulations are reactive deterrents that require user activity to take effect. Physical and information security measures also depend on users, but no one is perfect all the time. That is where information technology (IT) solutions come in. There is a plethora of IT solutions, specifically "technical controls," which "can enable and/or amplify policy enforcement where human behavior is difficult to regulate" [1].
Internet of Things (IoT) and Digital Forensics

Amazon Alexa devices, smart doorbells, and Wi-Fi enabled pace-makers have a few notable similarities. First, they simplify and automate redundant, necessary tasks for many Americans' lifestyle, security, and health. Second, they're all available at an affordable price, even after the COVID-19 pandemic. Most importantly, they're extremely portable wireless technologies capable of communicating with common consumer electronics including personal computers (PCs) and smartphones via wireless and cabled connections. That is the glory of “smart devices,” formally known as Internet of Things (IoT) devices.
After You Graduate From College

Congratulations, you've graduated from your university and are looking to capitalize on your new credential. Hopefully, you've done all of the things. Before you ditch your school login credentials, there are few things you should do first.
Drupal Security Tips

Drupal is quite secure from the start. Admittedly, I don't have deep experience with the Drupal content management system (CMS). I've only used it for testing features and comparing workflows to other website builders and applications. I like the Burndown kanban Drupal module. I know enough to help a new Drupal site owner who understands the importance of being proactive with website security. Below are some basic security recommendations.
Black Entrepreneurs, What if Shopify Goes Down?

This is not an inside scoop. It is a hypothetical case.
If you actively work on information security (InfoSec) at any point, you'll end up working on a disaster recovery (DR) and business continuity (BC) plan to maintain operations when the unexpected happens. You'll likely improve your system backup process or add security features. Hopefully, you at some point realize address the need for a backup plan in case your primary IT solution shuts down permanently.
Home Network Security Basics

Whether you're starting college or working on a new business, you'll benefit from applying basic best security practices. I'm going to simplify everything you should have on your personal computer (PC), why, and with recommendations so you're not left to figure it out on your own. Follow this cybersecurity guide and become less likely to be a victim.
Black Owned Businesses Need to Do These Things

I've learned a lot about how black entrepreneurs approach digital marketing since starting to support black-owned businesses, starting with D'iyanu, a few years ago. After purchasing products from over a dozen black-owned small businesses, I've realized some common mistakes that I'd like to share with everyone. I hope this helps small and medium-sized business (SMB) owners rethink how they approach digital marketing.
Bashblog Security

You're likely thinking one of the following:
- There's not much to securing a static site generator (SSG)
- The writer is spilling all their secrets
- What is Bashblog?
Yes, Bashblog is a static site generator. No, there isn't much to securing the Bashblog SSG by default. But embedded code and man-in-the-middle (MITM) attacks can cause vulnerabilities. You still have to harden the web server, especially if you run other services on your system. And to be fair, everything I mention below is public knowledge, if you know where to look. I'm going to show you where to look.
WordPress Security Tips
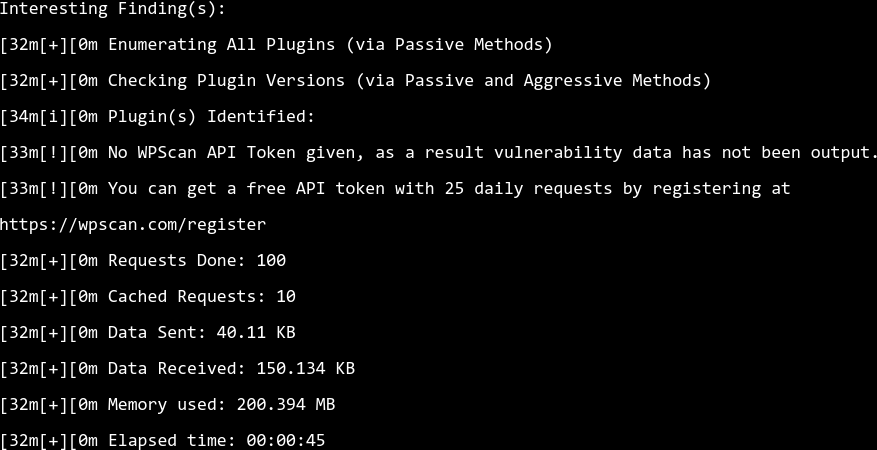
I know quite many people who love WordPress. I'm talking the self-hosted WordPress.org website builder you have to install on a web hosting server, not WordPress.com. But I don't hear them talk much about WordPress security.
I've mentioned some of the stuff below in other blogs about my favorite WordPress plugins and unnecessary plugins. And I don't want this to be verbose. So I'll try to keep everything straight-forward for newbies.
My Favorite Falkon Web Browser Features
Falkon, formerly known as Qupzilla, is a Chromium-based web browser for the KDE desktop environment (DE). Qupzilla was buggy and crashed at random when I tried it as a Linux newbie years ago. Falkon is a stable browser that makes compliments my needs for privacy and user experience (UX). I recommend it for anyone looking to try something new. Below are my four favorite Falkon browser features and extensions.
Matomo Analytics is Great-After I Remove Cookies
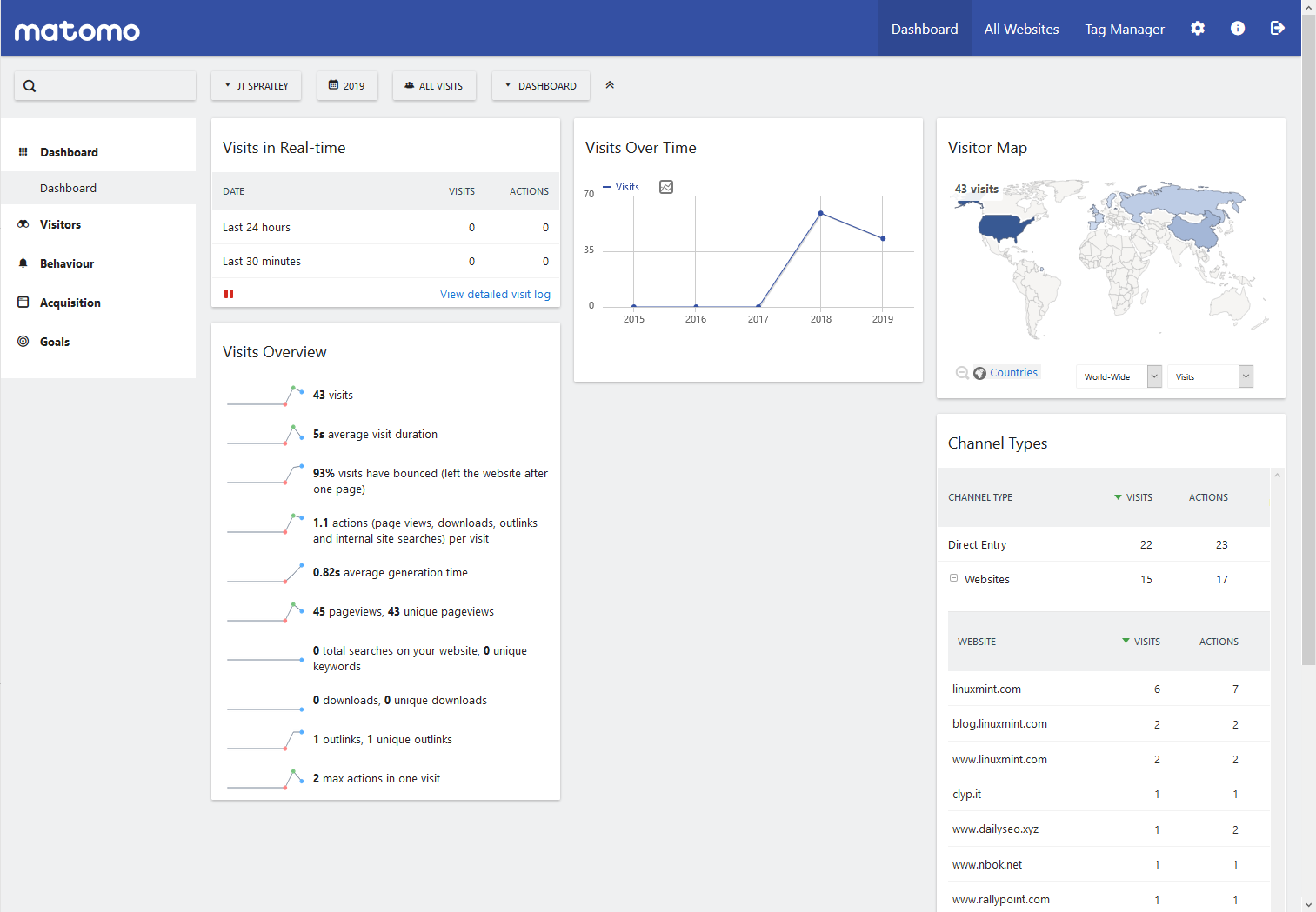
When I started looking into ways to improve visitor's privacy on my websites, I found 2 mysterious cookies with my browser developer tools (browser tab). When I looked them up, a WordPress GDPR plugin forum stated they were from Matomo Analytics. I confirmed the names of the cookies with Matomo's FAQ page: What are the cookies created by Matomo JavaScript Tracking client?
Creating RIPEMD-160 Checksums in Linux

RIPEMD (RIPE Message Digest) isn't as popular as SHA and MD5 for creating cryptographic hashes, or checksums. But I got curious after reading about it during some cybersecurity training. The md5sum and sha (256, 512, etc.) command-line hash (CLI) tools are pre-installed on many Linux distros. But I didn't see one for RIPEMD.
Cybersecurity Victim Blame Game

After reading "It's Time to Stop the Victim Blame Game" on DarkReading.com, I had to rethink some of my personal shopping rules. This part stuck out to me:
Upgrade-Movie Review

I watched this move twice before starting this blog. I’d watched it four times by the time I finished it.
Okay, Upgrade movie.
5 Best WordPress Plugins For My Goals

I’ve played with a lot of WordPress plugins. Some were good for convenience. Some were made obsolete with Gutenberg. Some became favorites as I learned how to integrate WordPress with so many different projects – podcasting, forums, school projects, web development, etc.
Below are 5 WordPress plugins I love and why.
Don’t Spread That Hoax!
First published on March 17, 2015
If you ever get bored, check out “Nonprofit.net/hoax – Don’t Spread That Hoax” for some random trivia, entertainment, myths, IT fun facts, and plenty of useless knowledge.
Computer Hard Drives-Keep, Wipe, and/or Destroy

First published on May 15, 2015
Whenever you sell a computer, don’t simply leave the hard drive with all your data easily recoverable. Ensure you keep the hard drive (HD) as a backup or external drive, wipe it properly so the data can’t be recovered, or destroy it completely with hammers, drills, and other manly stuff. I was on Craigslist earlier searching for a cheap laptop to buy so I can play with Linux. I found a guy looking to sell two laptops for ~$70 simply because his ex-girlfriend changed the log-in passwords. Hard Drives – Keep, wipe, and/or destroy it. But don’t simply give it, and all your information, away for free. Your credit score and mindset will thank you later.
What is Your Computer telling the Internet Right Now? BrowserSpy Answers
First published on September 10, 2015
If last weeks post spiked your interest in web security, privacy, and tracking, you should check out http://browserspy.dk/. Simply visit the site and the tabs (tests) on the left will educate you on what information your web browser is sharing.
I’m sure you’ll be surprised.
Unshorten that Tiny URL with UnShortening Tools
First published on September 21, 2015
Have you ever been on Facebook or Twitter and seen a short website address provided by a source that’s not completely professionally verified? For example, https://bit.ly/2AvtgLn. Called shortened or tiny URLs, it can save space anywhere, but it also hides the origin of the source.
Handling Bad Hard Drives (HDD or SSD)

First published on November 30, 2015
When you’re experiencing computer issues due to a failing hard drive, you have options:
5 Things I Learned from Using Google Ads

First published on September 19, 2016
Adsense / Google Ads
12 Types of WordPress Plugins You Don’t Need

First published on April 20, 2020
I’ve said this a few times in the past, but my goals to improve my WordPress blog taught me HTML and web design. I’ve downloaded a lot of WordPress plugins for extra features without knowing I could’ve achieved the same goal with a few lines of HTML or editing a file that already exists.
DuckDuckGo

First published on August 27, 2015
If you’re one of those people that are against privacy intrusion and unwanted tracking of your web browsing, replace Google with DuckDuckGo as your primary Web Search Engine. Simply go to DuckDuckGo.com and select the link at the bottom of the homepage. Read more about safeguarding your online activity below.
5 Directories Linux Users Should Back Up

Last updated on March 28, 2017
It’s always good to know what you need to back up before wiping a hard drive, whether you’re upgrading to a newer version of a distro (generally safer) or distro hopping (which I have 5 good reasons for doing a lot of).
Here’s a cheat sheet to help ensure you don’t forget anything.





