Internet of Things (IoT) and Digital Forensics

Amazon Alexa devices, smart doorbells, and Wi-Fi enabled pace-makers have a few notable similarities. First, they simplify and automate redundant, necessary tasks for many Americans' lifestyle, security, and health. Second, they're all available at an affordable price, even after the COVID-19 pandemic. Most importantly, they're extremely portable wireless technologies capable of communicating with common consumer electronics including personal computers (PCs) and smartphones via wireless and cabled connections. That is the glory of “smart devices,” formally known as Internet of Things (IoT) devices.
IoT is the concept of connecting physical objects - including vehicles, medical devices, and sports equipment - and people to seamlessly share data in a giant network [1]. Today, IoT devices are used in personal and commercial applications. Kitchen appliances and lighting systems are some of many products that increasingly include IoT features for home automation. Apple watches and fitness trackers assist people constantly on the go without regular access to a computer. Global positioning system (GPS) tracking in supply chain management and heating, ventilation and air conditioning (HVAC) monitoring for data center monitoring are standard commercial IoT use cases.
IoT setups are seeing growth in popularity because of the ways in which they save time and energy. IoT devices are generally as easy to initialize as common Bluetooth devices such as headsets, keyboards, and mice. This is partially because their software is oftentimes built on a lightweight Unix-like operating system (OS), or at least the kernel, with native cross-OS compatibility. Ensure it has internet access, complete the initial setup for the device, determine the best way to access its online portal remotely, and there's a new IoT environment. Afterwards, operations can be automated to work within more complex workflows with applications such as IFTTT, short for “If This Then That” [2]. That integration includes the ability to monitor device activity from a central location, allowing users to learn ways to optimize IoT systems for even greater convenience.
IoT hardware collect various types of data from their surroundings that can prove useful for forensic investigations. With a focus on network connectivity, location is naturally the most notable data type. Radio Frequency Identifier (RFID) tags and many aerial drones are developed specifically for GPS tracking. Flipper Zero and similar monitoring tools scan the area for unauthorized access points (rogue APs) or wireless office printers, [3] and report any broadcast info as directed. Lapel pins and even smaller trinkets can be converted into stealthy audio/video (AV) recorders that are barely visible to the naked eye. Camera images often include exchangeable image file format (EXIF) data including date and time taken, GPS data, and device information.
Individuals looking to get the biggest bang for their buck will utilize smart devices for everything possible. That sometimes leads to allowing smart digital assistants to manage contact information, emails, Short Message/Messaging Service (SMS) communications, and Voice over IP (VoIP) calls. Passcodes, personally identifiable information (PII), and personal health information (PHI) are readily shared with devices that could be compromised remotely. Companies commonly ship products with default settings to collect invasive usage data. For example, some smart TVs record nearby conversations if not manually disabled by the owner [4]. With the current state of artificial intelligence (AI), smart speaker data collection has been proven to help businesses build targeted ad campaigns specific to an individual [5].
IoT devices can provide a lot of information even with no network connection. Many devices use Secure Digital (SD) flash cards to store activity logs and other data. SD card data might include hidden folders which indicate the owner's system OS (e.g., macOS or Linux) used to manage it. Configuration settings can offer hints about the user's web accessibility requirements. Is high contrast mode enabled? Is the text size much larger than expected for the screen size? And of course, physical objects can carry fingerprints and other DNA for different lengths of time based on their material and environment. Notable mention: many smartphones handle most of these tasks for consumers.
There's a large variety of software and hardware capable of extracting IoT data, especially if physical access can be acquired through internet or cabled (USB, Ethernet, etc.) connection. OSForensics, Wireshark, and The Sleuth Kit and Autopsy are popular software with mobile forensics features [6]. The Kali Linux and CAINE (Computer Aided INvestigative Environment) OSes ship with dozens of penetration testing (pentesting) and digital forensics software, sparing forensics specialists from having to gather tools manually.
The lack of physical access only adds difficulty to manipulating a device. If any node on the network can be accessed in any way, it may be possible to compromise the network. Data packet sniffing and similar man-in-the-middle (MITM) attacks can acquire info useful for vulnerability analysis and successful cyber intrusion. A real-time spectrum analyzer can visualize emitted radio frequency (RF) waves to identify wireless devices with strong signal strength [7]. Bluetooth devices may be susceptible to data theft via Bluesnarfing [8]. Android and Apple products may be easier to breach by gaining access to the associated Google and Apple online account respectively. No wireless device connected to the internet is completely immune from cyber attacks.
There are cybersecurity best practices that have been proven to mitigate data breaches which can be applied to IoT setups. Many of these steps start with the initial setup process. Most “getting started” guides or software installation wizards will at some point prompt the user to create user credentials for authentication before completing administrative tasks. Hopefully, it allows for changing the administrative username from common phrases such as “admin” or “root.” Most users know the importance of using passwords over a dozen characters long, without PII, and with lower-case letters, upper-case letters, numbers, and symbols [9]. Unfortunately, this advice is followed less often when users prefer to remember multiple passwords. This discourages the use of complex passphrases for ones that are likely very similar to others the user attempts to remember. The easiest and most secure solution: use a password manager to create and maintain strong passwords and pin codes.
Any opportunity to reduce unnecessary permissions from unauthenticated internet users should be taken. If a use case requires creating user accounts for more than one person, they should only have the privileges needed to complete assigned tasks. This technical control, sometimes applied as an administrative control, is known as the least privilege principle. That the regular user accounts are using strong passwords and only capable of functions required should be verified before handed off to another user.
It's important to think about how to stop cyber attackers if they crack a password and gain unauthorized access. A quick way to improve security: multi-factor authentication (MFA) should be integrated to defend against brute-force login attacks when possible. MFA solutions verify users based on something they know (e.g., knowledge-based authentication or another pin code), have (smartphone or email access), do (a specific movement on a verification page), or are (face scan or other biometrics) [10]. If a smartphone application is used to administer the IoT device, authentication may also be granted based on somewhere they are. This means checking the user broadcast IP address with geolocation services to ensure they're in an expected, whitelisted location. Banks use this concept to report debit card purchases from suspicious locations. If this isn't available in the online portal, it might be worthwhile to reach out to the developers about adding the feature.
System logs and configuration file backups are usually ignored by less security-conscious tech users. Auditing device analytics allows users to understand usual usage metrics, detect anomalies, and assess how well security settings are working in totality. Ideally, those statistics could be aggregated with other IoT devices' usage into a security information and event management (SIEM) tool for “log management, intrusion detection, event correlation, threat intelligence gathering, incident management, compliance standard fulfillment, and vulnerability assessment processes” [11]. At the very least, logs should notify admin users of available updates.
Configuration backups come in handy when an anomaly indicates a data breach on the IoT network. In such cases, the best response could be to apply greater network security measures. It might only call for reducing device signal strength as a rate limiting solution. At worst, the best course of action might be to hard reset the device back to default settings. Having a verified backup file for IoT devices on another system which can be restored afterwards provides peace of mind for the worst case scenario. Together, implementing the least privilege principle, continuous verification of no malicious activity, and preparing for the worst case scenario make up what is known as the “zero trust” concept, [12] a fork of the “defense in depth” methodology.
Unfortunately, IoT firmware updates and native security settings are not always enough to discourage cyber attackers. For this reason, it is often recommended to complete manufacturer product registration for updates that can help improve the product. The company, or its parent company if applicable, may have a bug bounty program or bug reporting system which can serve as warnings for possible cyber attacks attempted on a particular model. Even an Really Simple Syndication (RSS) feed from the manufacturer blog can be beneficial for IoT security awareness.
If the IoT company is popular, there may be online communities on Reddit, Facebook, and other platforms dedicated to do-it-yourself (DIY) modifications. Between official and community communication channels, there should be many opportunities to discuss how to enhance IoT security posture. For example, are there efforts to further harden security the online portal and integration software? Can users regenerate their own Public Key Infrastructure (PKI) or Transport layer security (TLS) certificate, often mistakenly called the “SSL certificate,” for the web-based interface [14]?
If Wi-Fi is in use, are there ways to manually rate limit network activity and enforce the latest certain wireless communication? Is the password hashed before being stored? Can the password hashing algorithm be changed to something newer and harder to crack? A Secure Hash Algorithm 2 (SHA-2) hash function such as SHA512, or one of the less adopted SHA-3 hashes, is much stronger than SHA1 or the MD5 message-digest algorithm [13]. Is a salt added to passwords before they're hashed? If so, can the salt be changed manually? According to Open Worldwide Application Security Project (OWASP), Argon2id or bcrypt should be the first choices for password hashing functions because they automatically salt passwords [15]. Can they be used to store the IoT device login credentials?
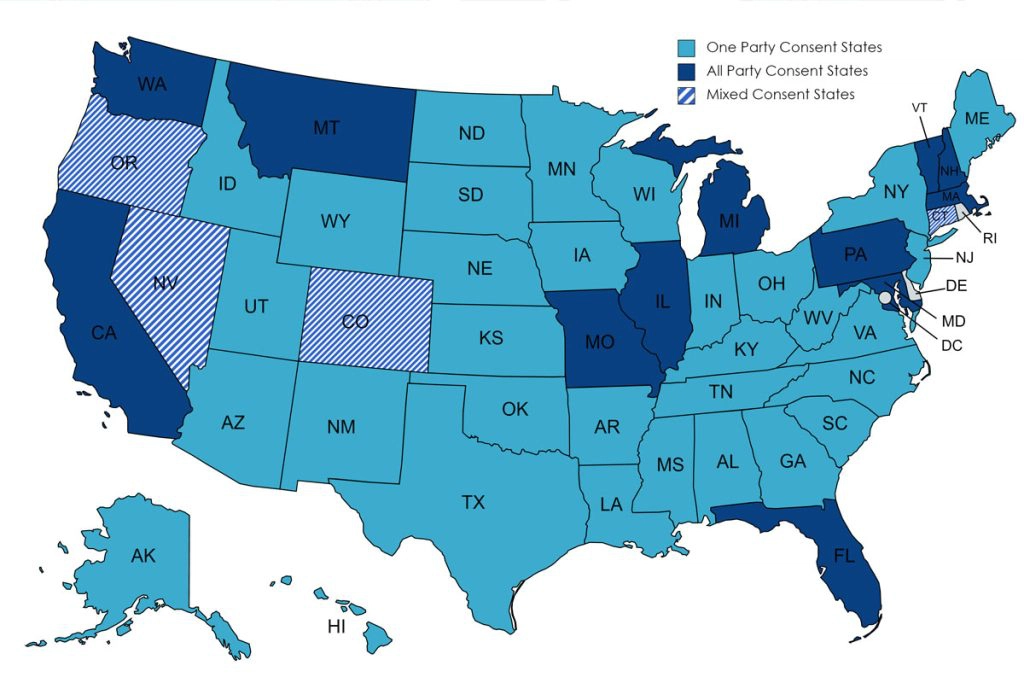
Depending on the location of the IoT network, state laws can provide an advantage or disadvantage. For example, most of the United States are one-party consent states, meaning that “an individual can record conversations they are a part of without the other person’s consent” [17]. Two-party, or “all-party,” states require the consent of all individuals being recorded for it to be legal. This law is the closest to governing controversial privacy concerns today related to mass surveillance and the rise of IoT usage.
It is unlawful to aim a surveillance camera at a neighbor's home where there is an expectation of privacy such as a bedroom window. However, one-party states do permit AV recording in areas with “no reasonable expectation of privacy” such as public parks and buildings. This legalizes AV recording public areas with GoPro cameras and similar products. Interestingly, this legality also authorizes doorbell cameras pointed at a neighbor's front door or garage in plain view. This introduces a legal gray area of personal surveillance opportunities as more alarm systems and lighting appliances are developed with IoT functions. Online security cameras can be pointed directly at a suspicious home and alert various remote systems and even local law enforcement when certain suspicious AV metrics are met.
Insecam.org and EarthCam.com are popular directories for viewing embeddable, online security cameras. Many are purposely open to the public. Some are not. Shodan.io and Censys.io crawl the web for various online systems, but do not embed live cameras in web-pages for easy previewing. Some listings lead to a web interface to allow manual camera adjustment or access to the login page.
On the offensive end, cameras in these directories can provide GPS coordinates, device info, and easy access to the online portal. This passive reconnaissance technique avoids analytics solutions up until a link leading to the camera portal is selected. Live feeds can be monitored and recorded without accessing the camera portal at all. On the defensive end, IoT device owners would want to deny this ease of intrusion. Some Hikvision cameras apply the “X-Frame-Options” security HTTP header, preventing browsers from embedding the feed on external sites like Insecam [19]. The manufacturer, or a user community, should be able to assist with configuring this on other models. Another option is to block scanner bots from Shodan and similar web crawling platforms from the network firewall [20].
The future of humanity with the Internet of Things looks different depending one's perspective and primary focus. On the positive side, IoT is saving people time and energy with more and more automation. Voice control boxes like the Amazon Dash button can instantly order essential goods. Smart thermostats remember and automatically set optimal internal temperatures based on external weather. The Amazon Kindle and other E-readers are replacing physical books in many homes to save storage space. And of course, Ring video doorbell cameras and their competitors have assisted many investigations and closed cases.
These examples are not without valid reasons for concern. Tech history shows a strong pattern of prioritizing convenience and accessibility over privacy and security against unauthorized users. From radio communications interception in world wars [22] to the Morris Worm infecting Advanced Research Projects Agency Network (ARPANET) in 1988 [23] to now drone-based cyber attacks [24], cybersecurity threats evolve alongside technology advances.
Worse, many great security improvements are still not used often. Domain Name System Security Extensions (DNSSEC) usage is trending upwards but still not widely enforced or well-known to consumers [25]. Most websites do not use “Content-Security-Policy” (CSP), “Permissions-Policy,” or “HTTP Strict-Transport-Security” (HSTS), HTTP response security headers capable of preventing code injection and HTTP downgrade attacks [26]. Far too many people who use tech daily show little to no concern about security risks because they feel there's nothing they can do about it anyway [27]. Tech innovators aren't stressing cybersecurity enough, and users aren't demanding it enough.
The seemingly pessimistic but unfortunate truth is that this will only get worse as more people trail-blaze human augmentation with bleeding edge IoT and AI tech. Smart prosthetic limbs that link better with the brain are becoming easier to develop [28]. Insulin pumps and heart pacemakers were proven to be susceptible to remote cyber attacks years ago [29]. Meanwhile, many are welcoming microchip implantation in their hands to replace their identification (ID), key, and debit cards [30]. Companies like Walletmor are working to make the process more accessible to everyone [31] while the Cyborg Foundation is pushing the cybergenetics movement [32].
With enough deviant creativity, cyber attacks on augmented humans can lead to their deaths. The 2018 “Upgrade” movie and 2014 “Shadowrun: Dragonfall” video game, both of the cyberpunk genre, do a good job of portraying the pros (productivity, interoperability, etc.) and cons (invasion of privacy and loss of body control) of “bio-hacking” oneself to “cyborg” status. These new challenges affect the realms of cybersecurity and biosecurity, which “involves securing valuable biological material from misuse or harm” [33]. Notable examples: PHI, biotechnology companies' use of AI in drug development, and agricultural processes for produce. This has led to a new field of study, cyberbiosecurity, which “aims to identify and mitigate security risks fostered by the digitization of biology and biotechnology automation” [34].
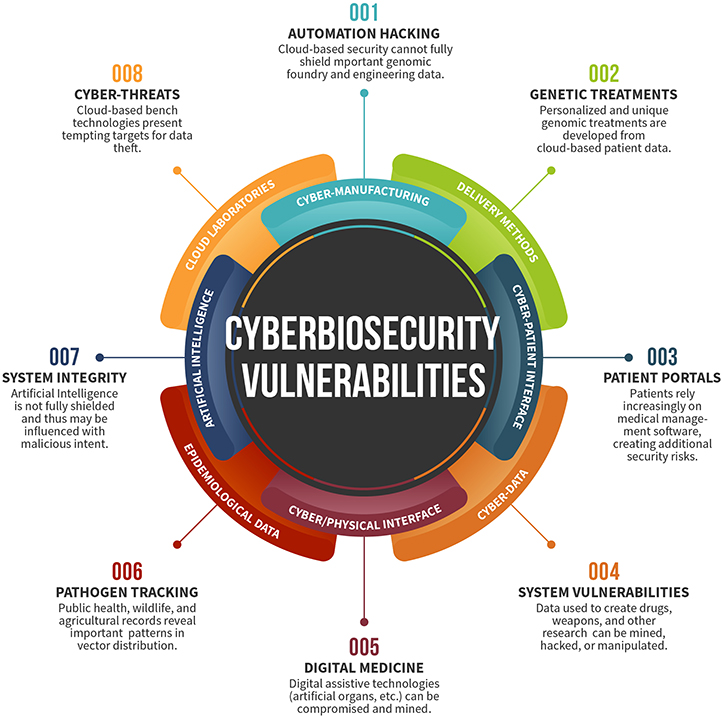
IoT devices store a grand amount of information about its environment, users, and nearby IoT systems. This big data aggregation can be used to improve lives and productivity workflows of millions. It can also be used to destroy them. Cyberbiosecurity will slowly become more important. One important question to ponder: will the society at large struggle to acknowledge and proactively mitigate cyberbiosecurity vulnerabilities, or learn from the decades-long history of cybersecurity attacks due to laziness, misconfiguration, and ignorance?
References
[1] J. Clark. “What is the Internet of Things (IoT)?” IBM, Nov. 27, 2016. [Online]. Available: https://www.ibm.com/blogs/internet-of-things/what-is-the-iot/. [Apr. 1, 2023].
[2] “What is IFTTT?” IFTTT. [Online]. Available: https://ifttt.com/explore/new_to_ifttt. [Apr. 1, 2023].
[3] “How to locate an access point.” Acrylic WiFi. [Online]. Available: https://www.acrylicwifi.com/en/blog/how-to-locate-an-access-point/. [Apr. 2, 2023].
[4] K. Komando. “Yes, your smart TV is spying on you – Here’s how to stop it.” Kim Komando Show, Oct. 29, 2022. [Online]. Available: https://www.komando.com/tech-tips/stop-smart-tv-tracking/544540/. [Apr. 2, 2023].
[5] J. Tuohy. “Researchers find Amazon uses Alexa voice data to target you with ads.” The Verge, Apr. 28, 2022. [Online]. Available: https://www.theverge.com/2022/4/28/23047026/amazon-alexa-voice-data-targeted-ads-research-report. [Apr. 3, 2023].
[6] D. Robb. “16 Best Digital Forensics Tools & Software.” eSecurity Planet, Jan. 19, 2023. [Online]. Available: https://www.esecurityplanet.com/products/digital-forensics-software/. [Apr. 4, 2023].
[7] R. Awati. “spectrum analyzer.” TechTarget, Jun. 2021. [Online]. Available: https://www.techtarget.com/searchnetworking/definition/spectrum-analyzer. [Apr. 6, 2023].
[8] A. Mohammed. “Linux Affected by Bluetooth Security Bug and It’s Serious. Kind of.” Fossbytes Media Pvt Ltd, Oct. 16, 2020. [Online]. Available: https://fossbytes.com/linux-bluetooth-security-bug-bleedingtooth/. [Apr. 6, 2023].
[9] M. Jančis. “How to create a good and strong password.” Cybernews, Apr. 5, 2023. [Online]. Available: https://cybernews.com/best-password-managers/how-to-create-a-strong-password/. [Apr. 6, 2023].
[10] “The 5 factors of authentication, and what you should know about them.” Red Key Solutions, Nov. 29, 2019. [Online]. Available: https://www.redkeysolutions.com/2019/11/the-5-factors-of-authentication-and-what-you-should-know-about-them/. [Apr. 7, 2023].
[11] “10 Best Free and Open-Source SIEM Tools.” DNSstuff, Nov. 24, 2019. [Online]. Available: https://www.dnsstuff.com/free-siem-tools. [Apr. 8, 2023].
[12] “Zero trust: An introduction for developers.” IBM, Mar. 13, 2023. [Online]. Available: https://developer.ibm.com/articles/zero-trust-introduction-for-developers/. [Apr. 8, 2023].
[13] D. Rhodes. “SHA-512 Hashing Algorithm Overview.” Komodo, Apr. 29, 2022. [Online]. Available: https://komodoplatform.com/en/academy/sha-512/. [Apr. 8, 2023].
[14] “PKI Certificate vs SSL: The Differences Explained.” DIYSecurityTips.com, Feb. 16, 2201. [Online]. Available: https://diysecuritytips.com/pki-certificate-vs-ssl-the-differences-explained/. [Apr. 8, 2023].
[15] “Password Storage Cheat Sheet.” OWASP. [Online]. Available: https://cheatsheetseries.owasp.org/cheatsheets/Password_Storage_Cheat_Sheet.html. [Apr. 8, 2023].
[16] O. Bastounis. “Ten... dual-band wireless routers.” The Register, Jun. 19, 2012. [Online]. Available: https://www.theregister.com/2012/06/19/review_ten_dual_band_wifi_routers/?page=6. [Apr. 8, 2023].
[17] “One-Party Consent States – Updated 2022.” Recording Law, Jan. 3, 2023. [Online]. Available: https://recordinglaw.com/united-states-recording-laws/one-party-consent-states/. [Apr. 8, 2023].
[18] “Live cameras: architecture.” Insecam. [Online]. Available: http://insecam.org/en/bytag/Architecture/. [Apr. 9, 2023].
[19] “Clickjacking Defense Cheat Sheet.” OWASP. [Online]. Available: https://cheatsheetseries.owasp.org/cheatsheets/Clickjacking_Defense_Cheat_Sheet.html. [Apr. 9, 2023].
[20] “How to block Shodan scanners.” IPFire Wiki, Feb. 16, 2023. [Online]. Available: https://wiki.ipfire.org/configuration/firewall/blockshodan. [Apr. 9, 2023].
[21] “Live camera Hua Hin, Thailand.” Insecam. [Online]. Available: [REDACTED FOR PRIVACY]. [Apr. 9, 2023].
[22] “The teenage radio enthusiasts who helped win World War II.” BBC, Jul. 5, 2013. [Online]. Available: https://www.bbc.com/news/technology-23162846. [Apr. 10, 2023].
[23] “Morris Worm.” HYPR Corp. [Online]. Available: https://www.hypr.com/security-encyclopedia/morris-worm. [Apr. 10, 2023].
[24] “Wi-Fi drones were used by hackers to penetrate a financial firm's network remotely.” TECHSPOT, Oct. 14, 2022. [Online]. Available: https://www.techspot.com/news/96321-drones-helped-hackers-penetrate-financial-firm-network-remotely.html. [Apr. 9, 2023].
[25] “DNSSEC and DANE Deployment Statistics.” DNSSEC-Tools. [Online]. Available: https://stats.dnssec-tools.org/#/https://stats.dnssec-tools.org/?top=dane&trend_tab=0. [Apr. 9, 2023].
[26] “Statistics.” GitHub, Apr. 2, 2023. [Online]. Available: https://github.com/oshp/oshp-stats/blob/main/stats.md. [Apr. 10, 2023].
[27] “2022 Consumer Cyber Readiness Report.” Consumer Reports. [Online]. Available: https://consumer-reports-ressh.cloudinary.com/image/upload/v1664551562/Consumer-Cyber-Readiness-Report-Final_edbv9f.pdf. [Apr. 10, 2023].
[28] M. Osborne. “This High Schooler Invented a Low-Cost, Mind-Controlled Prosthetic Arm.” Smithsonian Magazine, May 2, 2022. [Online]. Available: https://www.smithsonianmag.com/innovation/this-high-schooler-invented-a-low-cost-mind-controlled-prosthetic-arm-180979984/. [Apr. 11, 2023].
[29] M. Khera, “Think Like a Hacker,” Journal of Diabetes Science and Technology, vol. 11, no. 2, pp. 207–212, Dec. 2016, doi: https://doi.org/10.1177/1932296816677576. [Apr. 11, 2023].
[30] D. Hurd. “Why Thousands of Swedes Have Inserted Microchips Under Their Skin.” The Christian Broadcasting Network, Inc., Dec. 10, 2022. [Online]. Available: https://www2.cbn.com/news/world/why-thousands-swedes-have-inserted-microchips-under-their-skin. [Apr. 11, 2023].
[31] S. Berlin. “You Can Now Get a Payment Chip Implanted in Your Hand for $200.” Newsweek, Apr. 13, 2022. [Online]. Available: https://www.newsweek.com/you-can-now-get-payment-chip-implanted-your-hand-200-1697714. [Apr 11, 2023].
[32] Cyborg Foundation. Cyborg Foundation. [Online]. Available: https://www.cyborgfoundation.com/. [Apr. 11, 2023].
[33] L. C. Richardson, N. D. Connell, S. M. Lewis, E. Pauwels, and R. S. Murch, “Cyberbiosecurity: A Call for Cooperation in a New Threat Landscape,” Frontiers in Bioengineering and Biotechnology, vol. 7, Jun. 2019, doi: https://doi.org/10.3389/fbioe.2019.00099. [Apr. 11, 2023].
[34] S. Porter. “What is cyberbiosecurity?” Biotech-Careers, May 12, 2023. [Online]. Available: https://biotech-careers.org/articles/what-cyberbiosecurity. [Apr. 10, 2023].
Tags: cybersecurity, privacy, college, IT





