Why I Built a Privacy-First Workout Tracker (Gym Bag Digital)

Gym Bag Digital is an offline workout tracker for Android, by me. But why? There are a couple reasons I created the Gym Bag Digital Android app.
5 Cybersecurity Issues to Watch in 2024

Between the IBM
How Military Veterans Can Protect Themselves From Phishing and Other Online Scams

Military veterans are prime targets for personally identifiable information (PII). Businesses seek our Post 9/11 GI Bill because it's sure money. Employers see us as tax breaks. For as many benefits as we get between Veterans Affairs (VA) and the GI Bill, plenty others get an interesting bit of benefits from our presence. This is one of many reasons as to why military service members must be careful of how we share our military info.
Don't worry, non-technical folks, as I've done my best to simplify the best security practices, these days sometimes called the "Zero Trust" mindset, that I'll recommend in the key takeaways and video below. The overall solution: verify contacts supposedly from VA medical centers and community-based outpatient clinics (CBOCs).
Internet of Things (IoT) and Digital Forensics

Amazon Alexa devices, smart doorbells, and Wi-Fi enabled pace-makers have a few notable similarities. First, they simplify and automate redundant, necessary tasks for many Americans' lifestyle, security, and health. Second, they're all available at an affordable price, even after the COVID-19 pandemic. Most importantly, they're extremely portable wireless technologies capable of communicating with common consumer electronics including personal computers (PCs) and smartphones via wireless and cabled connections. That is the glory of “smart devices,” formally known as Internet of Things (IoT) devices.
Matomo Analytics is Great-After I Remove Cookies
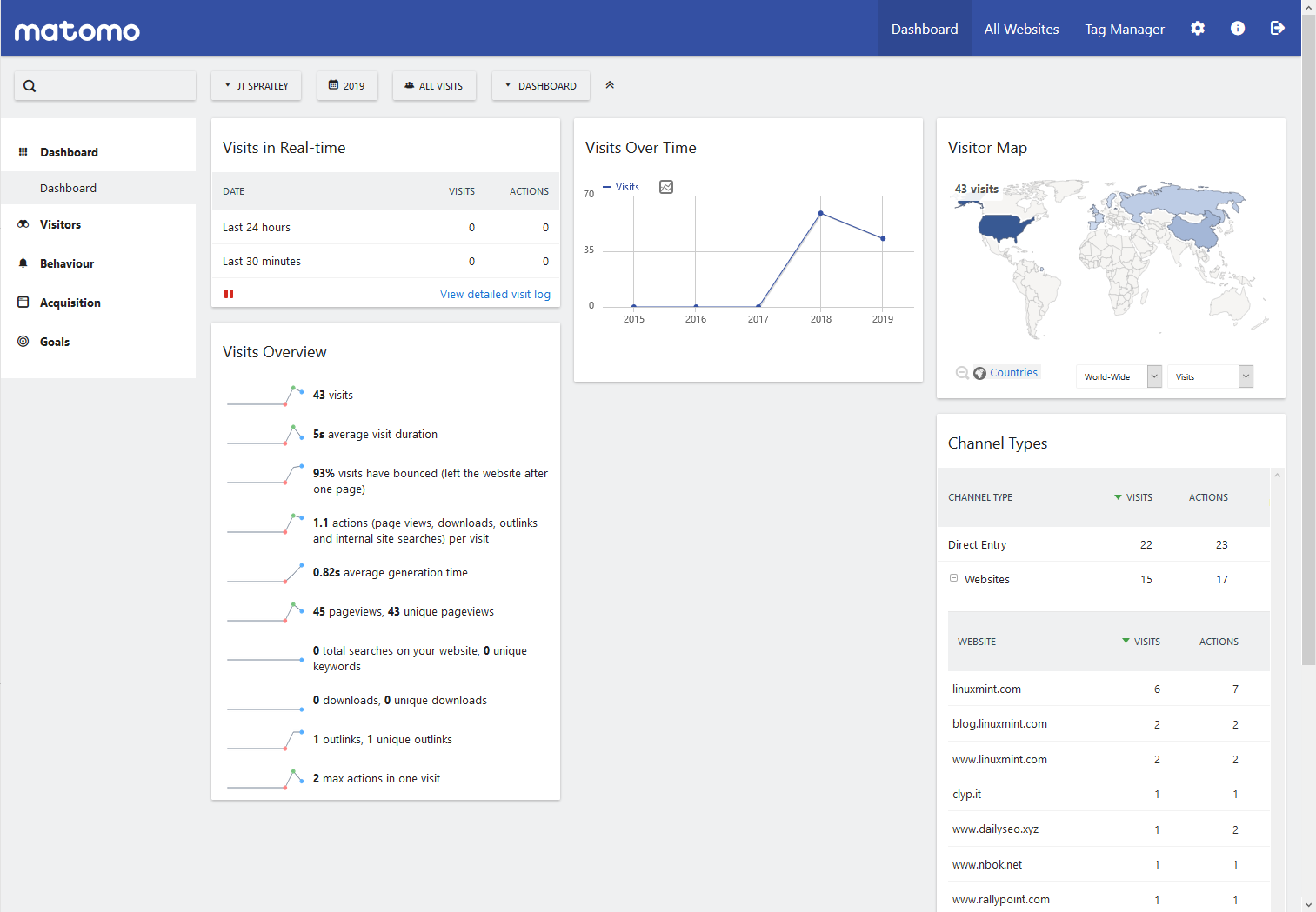
When I started looking into ways to improve visitor's privacy on my websites, I found 2 mysterious cookies with my browser developer tools (browser tab). When I looked them up, a WordPress GDPR plugin forum stated they were from Matomo Analytics. I confirmed the names of the cookies with Matomo's FAQ page: What are the cookies created by Matomo JavaScript Tracking client?
Cybersecurity Victim Blame Game

After reading "It's Time to Stop the Victim Blame Game" on DarkReading.com, I had to rethink some of my personal shopping rules. This part stuck out to me:
Don’t Spread That Hoax!
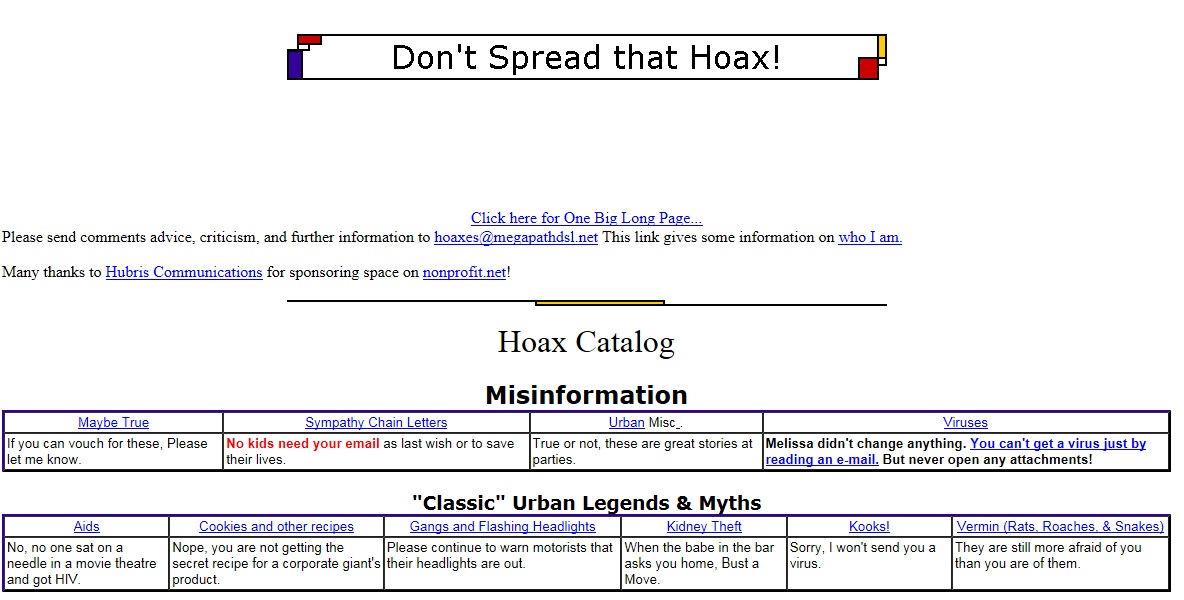
First published on March 17, 2015
If you ever get bored, check out “Nonprofit.net/hoax – Don’t Spread That Hoax” for some random trivia, entertainment, myths, IT fun facts, and plenty of useless knowledge.
Computer Hard Drives-Keep, Wipe, and/or Destroy

First published on May 15, 2015
Whenever you sell a computer, don’t simply leave the hard drive with all your data easily recoverable. Ensure you keep the hard drive (HD) as a backup or external drive, wipe it properly so the data can’t be recovered, or destroy it completely with hammers, drills, and other manly stuff. I was on Craigslist earlier searching for a cheap laptop to buy so I can play with Linux. I found a guy looking to sell two laptops for ~$70 simply because his ex-girlfriend changed the log-in passwords. Hard Drives – Keep, wipe, and/or destroy it. But don’t simply give it, and all your information, away for free. Your credit score and mindset will thank you later.
You’re Probably On CCTV Right Now

First published on June 18, 2015
I’ll just leave these links here. GO and ROAM may cause paranoia.
Website Improvements-Privacy Policy

First published on July 3, 2015
If I’m going to do something, I want to do it right. With the help of many domain scanners, I plan to achieve the standard of much fewer coding and regulation errors. My first step is adding a privacy policy that specifically states in a professional manner “I’m not invading your privacy.” Power Mapper pointed this out to me.
What is Your Computer telling the Internet Right Now? BrowserSpy Answers
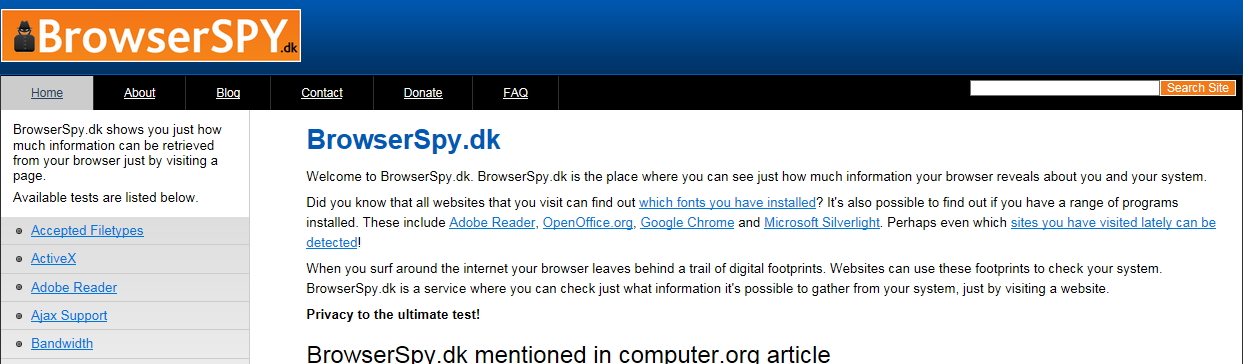
First published on September 10, 2015
If last weeks post spiked your interest in web security, privacy, and tracking, you should check out http://browserspy.dk/. Simply visit the site and the tabs (tests) on the left will educate you on what information your web browser is sharing.
I’m sure you’ll be surprised.
Unshorten that Tiny URL with UnShortening Tools
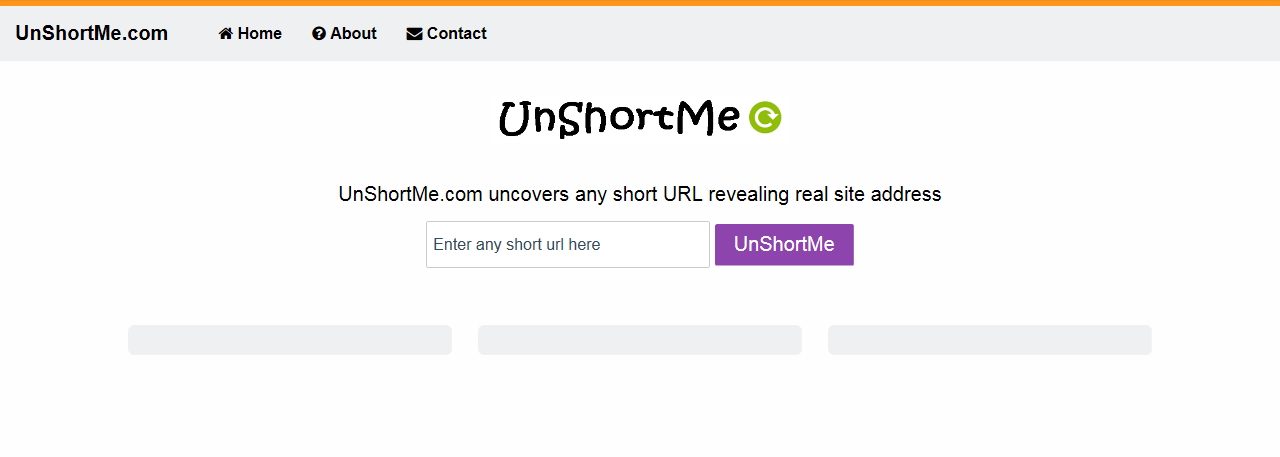
First published on September 21, 2015
Have you ever been on Facebook or Twitter and seen a short website address provided by a source that’s not completely professionally verified? For example, https://bit.ly/2AvtgLn. Called shortened or tiny URLs, it can save space anywhere, but it also hides the origin of the source.
Handling Bad Hard Drives (HDD or SSD)

First published on November 30, 2015
When you’re experiencing computer issues due to a failing hard drive, you have options:
5 Things I Learned from Using Google Ads

First published on September 19, 2016
Adsense / Google Ads
DuckDuckGo

First published on August 27, 2015
If you’re one of those people that are against privacy intrusion and unwanted tracking of your web browsing, replace Google with DuckDuckGo as your primary Web Search Engine. Simply go to DuckDuckGo.com and select the link at the bottom of the homepage. Read more about safeguarding your online activity below.





